Use Double SSH Tunnels Instead of VPN to Access Private Network
Use Double SSH Tunnels Instead of VPN to Access Private Network
Overview
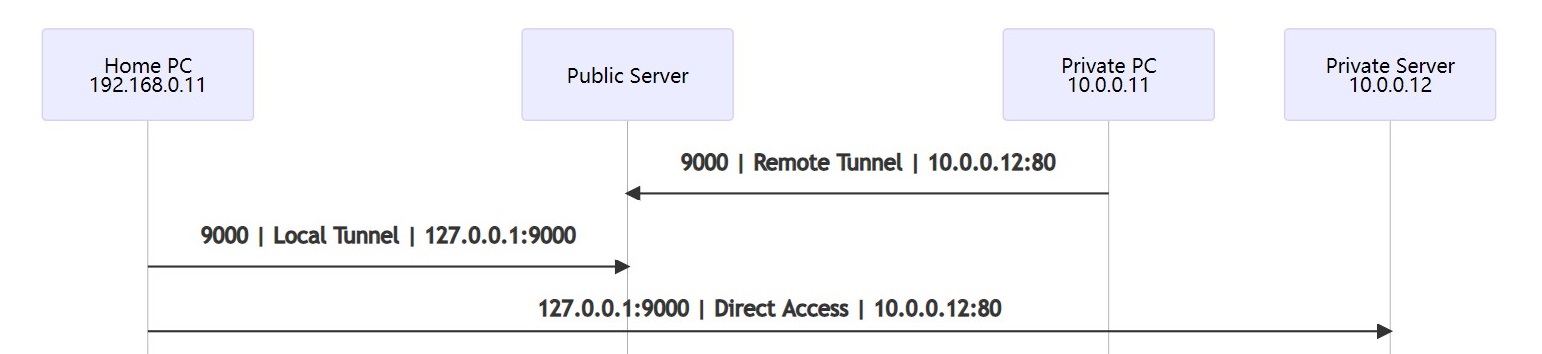
Imagine you have a corporate private network in 10.0.0.x, and you have a PC in the office (10.0.0.11) or any device that can run as an SSH client. You can use the office PC to create an SSH tunnel to a public Linux server (accessible on the internet) as a bridge to access other servers or devices in the office private network, such as an HTTP server (10.0.0.12).
Remote Tunnel
The first step is to create a remote tunnel from the office PC 10.0.0.11 to the public server, e.g. yourserver.com. Assume you access the public server with an SSH key (sshkey.pem).
Run this command on your office PC if it is a Linux:
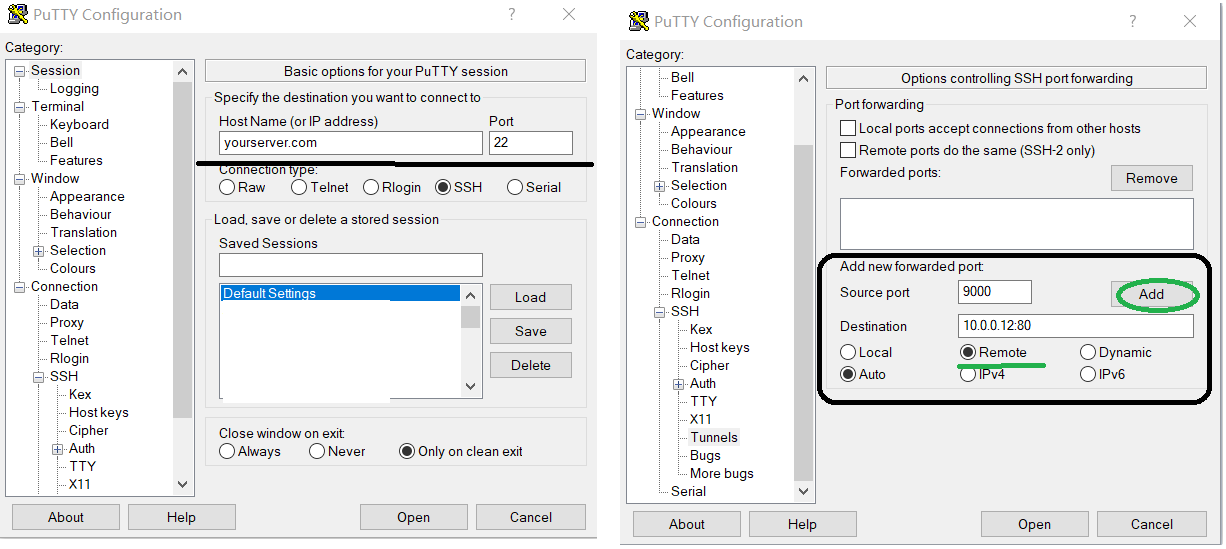
-R 9000:10.0.0.12:80 This creates a remote tunnel and the public server is listening on port 9000. When you access the port 9000 on the public server, it is redirected to the private server 10.0.0.12 on port 80 (HTTP) via office PC 10.0.0.11. Note that for security reasons the port 9000 is listening only on localhost 127.0.0.1, not all IP addresses 0.0.0.0 on the server. Run netstat -anp|grep 9000 on the public server and you will see that as follows.
-f -N This is optional.
The -f option tells the ssh command to run in the background and -N not to execute a remote command.
Now if you SSH into your public server, you can access the private HTTP server 10.0.0.12:80 with local port 9000. Test with curl 127.0.0.1:9000 or wget 127.0.0.1:9000 and you should get the home page of 10.0.0.12:80.
If your private office PC is a Windows, install putty and open an ssh session to your public server with the below tunnel settings.
Local Tunnel
The second step is to create a local tunnel from your home PC 192.168.0.11 to the public server (yourserver.com) so that you can access the private HTTP server 10.0.0.12:80 directly from your home PC, using the public server as a bridge.
Run this command on your home PC if it is a Linux:
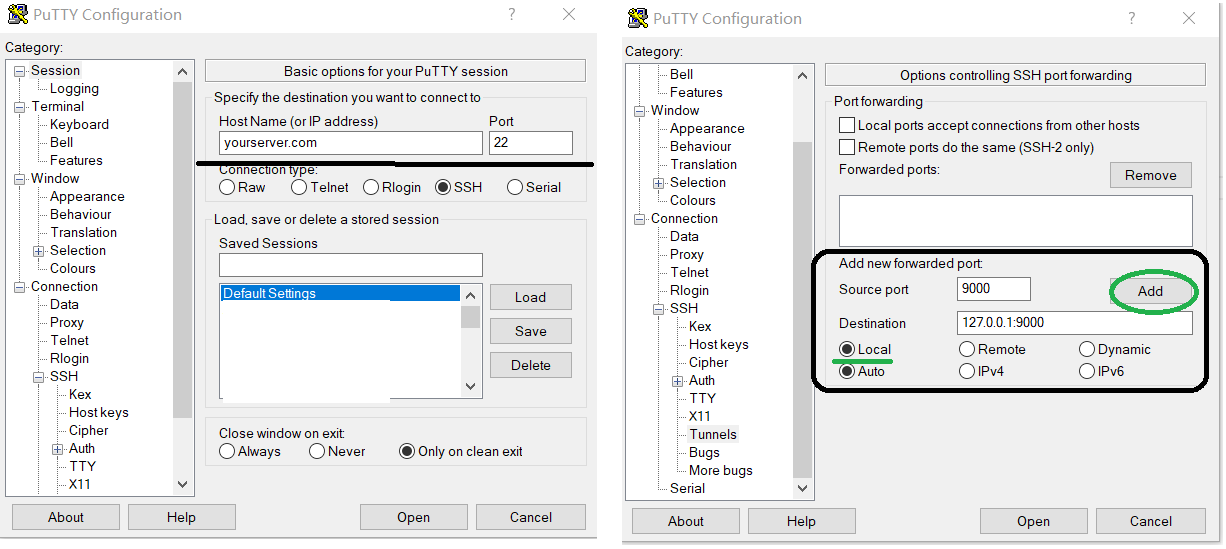
-L 9000:127.0.0.1:9000 This creates a local tunnel and your home PC is listening on port 9000. When you access the port 9000 on your home PC, it is redirected to the public server local port 127.0.0.1:9000, then to the the private server 10.0.0.12:80 via the remote tunnel created above. That's the magic 😉
Run netstat -an|grep 9000 on your home PC and you will see it listens on port 9000 as follows.
Now open a web browser from your home PC and enter http://127.0.0.1:9000, and you will see the magic that it shows the home page of the private HTTP server (http://10.0.0.12) directly.
Note that the same approach works with a private FTP server, ssh server, etc., just change the destination port in the remote tunnel.
If your home PC is a Windows, install putty and open an ssh session to your public server with the below tunnel settings.
Google Remote Desktop
If it feels too technical for you to set up or you simply don’t have any Linux public server, I would recommend using Google Remote Desktop https://remotedesktop.google.com to access your office PC without VPN. Just visit that URL in the Chrome browser in both your office PC and home PC to set it up. And it will start the service on system bootup, so no worries about system auto reboot.
Note
This is also published at https://medium.com/@peter-jp-xie/use-double-ssh-tunnels-instead-of-vpn-to-access-private-network-f0dee50d82e3.
